Why Your Outdated Windows Servers Are Putting Your Business at Risk
Would you trust an airplane with critical failures to get you safely to your destination? Then why trust your Windows Server 2012 R2 to keep your business secure? With over 35 critical vulnerabilities, running end-of-life systems could be your organization's greatest risk. Discover how to protect your infrastructure before it’s too late – because in today’s threat landscape, there’s no room for error.

Windows Servers vs Airplane
Imagine boarding an airplane that’s long out of service, plagued with over 35 critical mechanical issues. Would you still feel safe? Now think of your Windows Server 2012 R2. It’s essentially that same outdated airplane, riddled with vulnerabilities, but this time, it’s your organization’s infrastructure on the line.
It’s time to act – don’t waste any more time. Your flight is booked, but it’s at serious risk.
Understand the Security Implications and Potential Impact
Security Score Impact: End-of-Life (EOL) systems significantly lower your organization’s overall security score.
Massive Risk: These systems are highly vulnerable to attacks due to the absence of updates and vendor support, posing a severe threat to the entire corporate environment.
Attackers love EOL operating systems, as they serve as open invitations to gain a foothold in your network, potentially leading to a full infrastructure compromise.
While our APT Response services can help you recover, we always advocate for a proactive approach—one that ensures you never face such a situation in the first place.
Identify EOL Systems in Your Organization
Discovery & Methods to Identify End-of-Life (EOL) Operating Systems
Start with discovery. We frequently uncover End-of-Life (EOL) operating systems during our assessments, whether through preventive services like AD/EID or our managed CSOC offerings. The first step in addressing this issue is developing reliable methods to identify EOL systems and take action.
It’s crucial to establish a strategy for regularly identifying these outdated systems using various tools and assessments. We can partner with you to implement this effectively.
One key step is identifying your Line of Business (LOB) applications and determining where they’re running to ensure alignment with your business needs. The risk-based LOB triangle is a valuable tool that helps uncover dependencies and assess risks throughout your organization.
By analyzing loss patterns and volatility over time, this approach becomes a cornerstone of effective risk management, delivering essential insights to your management team. This is especially critical when super-sensitive LOBs, sitting at the top of the triangle, are operating on EOL systems. These systems pose a significant threat to service continuity, operational stability, and overall business performance.
In short, if your most critical LOBs are running on EOL systems, you’re exposing your company to the risk of service disruption and elevated operational dangers.
Building an Outdated Operating System Strategy
Short-Term Solution: ESU Could Be Your Friend
Address vulnerabilities by implementing a short-term solution and simultaneously work on a long-term strategy to handle End-of-Life (EOL) and End-of-Support (EOS) systems.
Use Extended Security Updates (ESU) as a lifesaver to get through this challenging period. ESU can temporarily secure EOL systems until migration or decommissioning is completed. Remember, this is just a short-term workaround.
Isolation: Completely isolate these systems from networks and Active Directory during the transition period. This gives you the time to plan and execute your migration without exposing yourself to severe risks, creating a more manageable situation.
Build a Long-Term Strategy
After addressing immediate concerns with ESU, it’s time to shift focus towards a long-term strategy to phase out legacy systems. Take a moment to evaluate the best long-term solutions that align with your needs.
Consider migration to modern operating systems, serverless approaches, Software as a Service (SaaS), or any cloud-native solutions that tailored to your environment.
Migration: Plan and execute the upgrade of outdated systems to the latest versions. Evaluate alternatives such as serverless, containers, or Kubernetes (K8s). glueckkanja’s Azure Foundation Blueprint provides a solid framework for your cloud migration. Using Infrastructure-as-Code deployment, we ensure a fast implementation with the highest quality. Security and governance requirements are directly embedded in the platform, and built-in controls such as policies and automation replace outdated, costly processes and workflows.
Decommissioning: Safely decommission unsupported systems.
By following this approach, you mitigate immediate risks while planning for sustainable, long-term security improvements. If you need further details or assistance, feel free to reach out!
Long-Term Target: In the future, ensure you are prepared well in advance of your systems reaching End of Life (EOL).
Get in contact with our Azure experts: Plan and execute a successful cloud migration with our guidance. glueckkanja holds the Azure Advanced Specialization for Infrastructure and Database Migration. Customers can also take advantage of the Azure Migration and Modernization Program (AMM) for comprehensive migration support.
Know About OS Support Lifecycle
Regularly review the support lifecycle and timeline for each operating system (OS) to ensure compliance and proactive risk management.
Microsoft provides consistent and predictable guidelines for their products, whether it’s server OS, client OS, or other products like Exchange, SQL, and many more.
This enables strategic planning for the future. Always stay informed about the OS and software support lifecycle. Regular reviews help you stay compliant and proactively manage risks. With Defender for Endpoint, these reviews are simplified. Monitoring vulnerabilities and identifying End-of-Life systems are integral parts of our CSOC Service.
Get an overview of the Microsoft Lifecycle Policy.
Conclusion: Don’t Wait for the Press to Write Your Story
The message is loud and clear: don’t wait for service interruptions or compromises.
We hope to see only positive news about your enterprise in the press. While we offer APT Response services, we strongly encourage you – and all our customers – to engage with us proactively, rather than reacting to a security breach.
The essence of this article is to urge you to shift from a reactive stance to preparing your business for the next level. Future-proof your organization by maintaining up-to-date platforms or adopting cloud-native solutions. All stakeholders, including your customers and management, will appreciate this proactive approach.
Management, in particular, should be fully aware of their responsibilities and liabilities in ensuring the company’s operational stability and security.
Take advantage of our Azure, Workplace, and Security offerings – feel free to reach out to us!
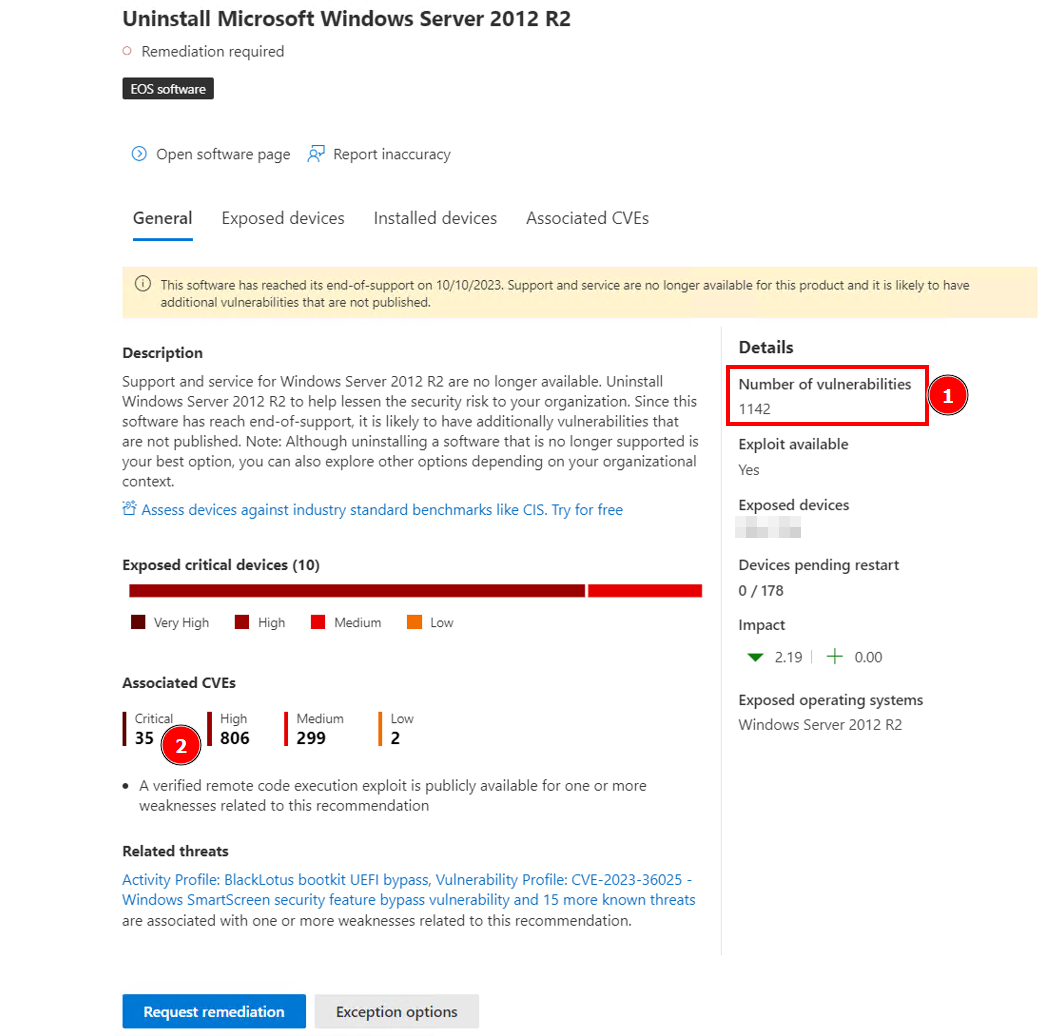
Appendix - Windows Server 2012 R2 - Windows Server 2008 R2 - Number of Vulnerabilities
The table below highlights the known vulnerabilities, which continue to increase by over 20 each month.
| Operating System | Windows Server 2012 R2 | Windows Server 2008 R2 |
|---|---|---|
| Total # of Vulnerabilities* | 1.142 | 2.240 |
| Critical | 35 | 47 |
| High | 806 | 1.457 |
Data as of September 2024, with a growing number of vulnerabilities month-over-month
As of September 2024, Windows Server 2012 R2 is missing 1,142 vulnerabilities (see bullet point 1), which remain unaddressed or unpatched. This number is steadily growing month over month, with 35 classified as critical and 806 as high severity (see bullet point 2).
The situation is even more concerning for Windows Server 2008 R2, with an even larger number of known vulnerabilities. This creates an inviting opportunity for attackers, giving them a clear path to potential compromises.
This data is sourced from Microsoft Defender for Endpoint, which provides a comprehensive overview and valuable insights into system vulnerabilities.